OpenMediaVault Permissions
In the Gargoyle Router Firmware video I walked through the Gargoyle firmware and explained how and why I organize my network with hostnames. In this post I will be showing how I setup my ACL’s or user/file permissions on my OpenMediaVault server for the devices that use it.
First let’s look at an overview of a sample network.
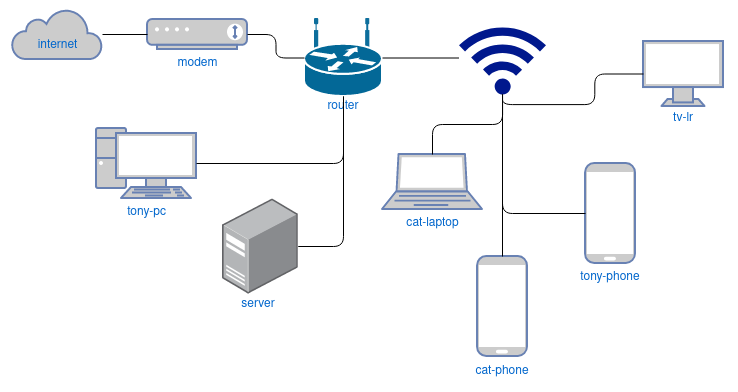
This is a simplistic overview, but you can get an idea of the different types of devices on my network and their respective hostnames. Most of these devices need to interact with the OpenMediaVault server which hosts a number of services. The list of services provided can be seen in the post Favorite Self-hosted Services.
Many of the devices on the network need access to the files on the server, but every device or user shouldn’t have access to every file. In order to solve for this and keep things organized, I make a username for each device based on it’s hostname that needs access to the shares. Below is a table of a few devices for you to visualize this.
| Device | Hostname | OMV User |
|---|---|---|
| my phone | tony-phone | tony-phone |
| my pc | tony-pc | tony-pc |
| living room tv | lr-tv | lr-tv |
| girlfriend’s phone | cat-phone | cat-phone |
| girlfriend’s laptop | cat-laptop | cat-laptop |
It’s an easy scheme to remember, basically $user-$device or $location-$device, and now we can be specific with both who and what devices have access to specific files. I’m going to provide some examples, but first let me lay out a few example shares:
//backups
//backups/tony
//backups cat
//media
//media/movies
//media/tv
//media/music
//media/pictures
//public
-
Users cat-pc, cat-laptop, cat-phone have full read/write access to //backups/cat so she can make backups from these devices to this directory but none of my user accounts nor any other accounts have access to it. There is absolutely no reason my user accounts need to have access to her backup directory. And vise versa, users tony-pc, tony-laptop, tony-phone have full read/write access to //backups/tony but no other users have access to it.
-
Her phone, user cat-phone can read //media/movies but it can not write to it. She does not need to write to the folder with her phone. But her laptop, user cat-laptop has read/write permissions to it because she often downloads movies from the laptop to it.
-
The living room TV, user lr-tv, can read but not write to //media/. The TV does not need write access to play movies and TV shows.
-
Every device or username has read/write to //public, this can be used to transfer files between devices quickly without worrying about user permissions. For instance, if I’m on my laptop and come across a config or apk that the TV needs, I can just download it to //public and then open it from //public on the TV. //public has become a somewhat organized folder on it’s own through this repeated process with a lot of useful files.
These are just a few examples but hopefully it gives an idea of how much control you can have over the access to the files on your NAS by setting up proper ACL’s or user/file permissions. But why do this? I do it for two reasons:
-
It can prevent accidental deletions and/or other mistakes. This is the biggest reason for doing it.
-
It could also potentially make it easier to identify rogue or compromised devices.
